# Fix 16/03/2015(D/M/Y)
# NET-GAME 2WAN "Static" V.5.1
# Script Support RouterOS V.6.15 - 6.27
========================================================================
# Features
# 1.Net-Game
# 2.RouteOver
# 3.FailOver( DNS & GateWay )
# 4.Block brute force attacks to the routers via SSH, Telnet, and Winbox
# 5.Service
# 6.Traffic Priotization
# 7.Joy Dota ( IP Public Dota )
# 8.Remote CCTV
# 9.Block DNS
# 10.Block UltraSurf
# 11.Block Hotspot Shield
# 12.Block PSP&Torrent
# 13.Block WEB&DNS Torrent
# 14.Block WEB&DNS ProGame
# 15.Block Baidu
# 16.Block Virus
# 17.QOS Client
# 18.QOS HTTP&HTTPS
# 19.QOS Youtube/Video/Stream
# 20.QOS Download File
========================================================================
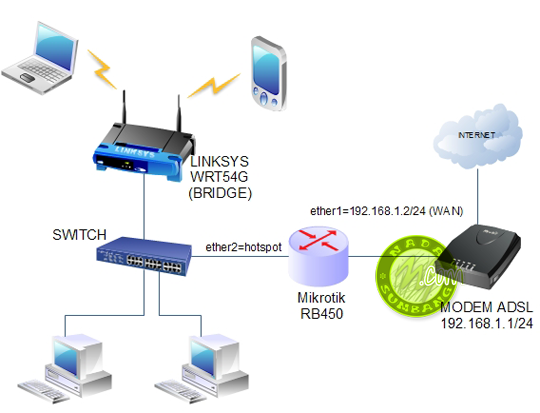
# NET WAN1 192.168.1.2
# GAME WAN2 192.168.2.2
# Local 192.168.10.10-200
# Mikrotik RB750,RB450,RB2011, CCR1009-8G-1S CCR1009-8G-1S-1S+ RouterOS License
# Set Ethernet
/interface ethernet
set [ find default-name=ether1 ] name=WAN1 comment="ETH_1"
set [ find default-name=ether2 ] name=WAN2 comment="ETH_2"
set [ find default-name=ether3 ] name=ether3 comment="ETH_3"
set [ find default-name=ether4 ] name=ether4 comment="ETH_4"
set [ find default-name=ether5 ] name=Local comment="ETH_5"
/
# Set IP Address Interface WAN1,WAN2,Local
/ip address
add address=192.168.10.1/24 network=192.168.10.0 broadcast=192.168.10.255 interface=Local
add address=192.168.1.2/24 network=192.168.1.0 broadcast=192.168.1.255 interface=WAN1
add address=192.168.2.2/24 network=192.168.2.0 broadcast=192.168.2.255 interface=WAN2
/
# Input
/ip firewall mangle
add chain=input in-interface=WAN1 action=mark-connection new-connection-mark=WAN1_conn
add chain=input in-interface=WAN2 action=mark-connection new-connection-mark=WAN2_conn
/
# Output
/ip firewall mangle
add chain=output connection-mark=WAN1_conn action=mark-routing new-routing-mark=to_WAN1
add chain=output connection-mark=WAN2_conn action=mark-routing new-routing-mark=to_WAN2
/
# Accept
/ip firewall mangle
add chain=prerouting dst-address=192.168.1.0/24 action=accept in-interface=Local
add chain=prerouting dst-address=192.168.2.0/24 action=accept in-interface=Local
/
# Set Priority & DSCP
/ip firewall address-list
add address=192.168.10.0/24 list="Network Admins" disabled=no
add address=192.168.10.0/24 list="Network Tunnels" disabled=no
/
/ip firewall mangle
add action=change-dscp chain=input comment="DSCP - 7 - API Port 8728 (Local Management)" dst-port=8728 new-dscp=7 protocol=tcp
add action=change-dscp chain=input comment="DSCP - 7 - Secure Web Access Port 443 (Local Management)" dst-port=443 new-dscp=7 protocol=tcp
add action=change-dscp chain=input comment="DSCP - 7 - Web Access Port 80 (Local Management)" dst-port=80 new-dscp=7 protocol=tcp
add action=change-dscp chain=input comment="DSCP - 7 - Winbox Port 8291 (Local Management)" dst-port=8291 new-dscp=7 protocol=tcp
add action=change-dscp chain=input comment="DSCP - 7 - Telnet Port 23 (Local Management)" dst-port=23 new-dscp=7 protocol=tcp
add action=change-dscp chain=input comment="DSCP - 7 - SSH Port 22 (Local Management)" dst-port=22 new-dscp=7 protocol=tcp
add action=change-dscp chain=input comment="DSCP - 7 - FTP Port 21 (Local Management)" dst-port=21 new-dscp=7 protocol=tcp
add action=change-dscp chain=forward comment="DSCP - 7 - API Port 8728 (Remote Managemenet)" dst-port=8728 new-dscp=7 protocol=tcp src-address-list="Network Admins"
add action=change-dscp chain=forward comment="DSCP - 7 - Secure Web Access Port 443 (Remote Managemenet)" dst-port=443 new-dscp=7 protocol=tcp src-address-list="Network Admins"
add action=change-dscp chain=forward comment="DSCP - 7 - Web Access Port 80 (Remote Managemenet)" dst-port=80 new-dscp=7 protocol=tcp src-address-list="Network Admins"
add action=change-dscp chain=forward comment="DSCP - 7 - Winbox Port 8291 (Remote Managemenet)" dst-port=8291 new-dscp=7 protocol=tcp src-address-list="Network Admins"
add action=change-dscp chain=forward comment="DSCP - 7 - Telnet Port 23 (Remote Managemenet)" dst-port=23 new-dscp=7 protocol=tcp src-address-list="Network Admins"
add action=change-dscp chain=forward comment="DSCP - 7 - SSH Port 22 (Remote Managemenet)" dst-port=22 new-dscp=7 protocol=tcp src-address-list="Network Admins"
add action=change-dscp chain=forward comment="DSCP - 7 - FTP Port 21 (Remote Managemenet)" dst-port=21 new-dscp=7 protocol=tcp src-address-list="Network Admins"
add action=change-dscp chain=forward comment="DSCP - 6 - PPTP Port 1723 (LAN Traffic)" new-dscp=5 port=1723 protocol=tcp
add action=change-dscp chain=forward comment="DSCP - 6 - GRE Protocol (LAN Traffic)" new-dscp=5 protocol=gre
add action=change-dscp chain=forward comment="DSCP - 6 - L2TP UDP Port 500 (LAN Traffic)" new-dscp=5 port=500 protocol=udp
add action=change-dscp chain=forward comment="DSCP - 6 - L2TP UDP Port 1701 (LAN Traffic)" new-dscp=5 port=1701 protocol=udp
add action=change-dscp chain=forward comment="DSCP - 6 - L2TP UDP Port 4500 (LAN Traffic)" new-dscp=5 port=4500 protocol=udp
add action=change-dscp chain=forward comment="DSCP - 6 - OVPN TCP Port 1194 (LAN Traffic)" new-dscp=5 port=1194 protocol=tcp
add action=change-dscp chain=forward comment="DSCP - 5 - SSTP TCP Port 443 (LAN Traffic)" new-dscp=5 port=443 protocol=tcp
add action=change-dscp chain=prerouting comment="DSCP - 6 - PPTP Port 1723 (Local Management)" new-dscp=6 port=1723 protocol=tcp src-address-list="Network Tunnels"
add action=change-dscp chain=prerouting comment="DSCP - 6 - GRE Protocol (Local Management)" new-dscp=6 protocol=gre src-address-list="Network Tunnels"
add action=change-dscp chain=prerouting comment="DSCP - 6 - L2TP UDP Port 500 (Local Management)" new-dscp=6 port=500 protocol=udp src-address-list="Network Tunnels"
add action=change-dscp chain=prerouting comment="DSCP - 6 - L2TP UDP Port 1701 (Local Management)" new-dscp=6 port=1701 protocol=udp src-address-list="Network Tunnels"
add action=change-dscp chain=prerouting comment="DSCP - 6 - L2TP UDP Port 4500 (Local Management)" new-dscp=6 port=4500 protocol=udp src-address-list="Network Tunnels"
add action=change-dscp chain=prerouting comment="DSCP - 6 - OVPN TCP Port 1194 (Local Management)" new-dscp=6 port=1194 protocol=tcp src-address-list="Network Tunnels"
add action=change-dscp chain=prerouting comment="DSCP - 5 - SSTP TCP Port 443 (Local Management)" new-dscp=5 port=443 protocol=tcp src-address-list="Network Tunnels"
add action=change-dscp chain=postrouting comment="DSCP - 7 - Skype, HTTPS" disabled=no dst-port=443 new-dscp=7 passthrough=yes protocol=tcp
add action=change-dscp chain=postrouting comment="DSCP - 7 - VOIP" disabled=no new-dscp=7 passthrough=yes port=1167,1719,1720,8010 protocol=udp
add action=change-dscp chain=postrouting comment="DSCP - 7 - VOIP" disabled=no new-dscp=7 passthrough=yes port=1719,1720,8008,8009 protocol=tcp
add action=change-dscp chain=postrouting comment="DSCP - 7 - SIP" disabled=no new-dscp=7 passthrough=yes port=5060 protocol=tcp
add action=change-dscp chain=postrouting comment="DSCP - 7 - SIP" disabled=no new-dscp=7 passthrough=yes port=5060 protocol=udp
add action=change-dscp chain=postrouting comment="DSCP - 7 - SIP 5004" disabled=no new-dscp=7 passthrough=yes port=5004 protocol=udp
add action=change-dscp chain=postrouting comment="Priority - 7 - Ventrilo VOIP" disabled=no new-priority=7 passthrough=yes port=3784 protocol=tcp
add action=change-dscp chain=postrouting comment="Priority - 7 - Ventrilo VOIP" disabled=no new-priority=7 passthrough=yes port=3784,3785 protocol=udp
add action=change-dscp chain=postrouting comment="Priority - 7 - Windows Live Messenger Voice" disabled=no new-priority=7 passthrough=yes port=6901 protocol=tcp
add action=change-dscp chain=postrouting comment="Priority - 7 - Windows Live Messenger Voice" disabled=no new-priority=7 passthrough=yes port=6901 protocol=udp
add action=set-priority chain=prerouting comment="Priority - 6 - SSH" disabled=no new-priority=6 passthrough=yes port=22 protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 6 - Telnet" disabled=no new-priority=6 passthrough=yes port=23 protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 6 - ICMP" disabled=no new-priority=6 passthrough=yes protocol=icmp
add action=set-priority chain=prerouting comment="Priority - 6 - TCP DNS Requests" disabled=no new-priority=6 passthrough=yes port=53 protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 6 - UDP DNS & mDNS Requests" disabled=no new-priority=6 passthrough=yes port=53,5353 protocol=udp
add action=set-priority chain=prerouting comment="Priority - 6 - PPTP VPNs" disabled=no new-priority=6 passthrough=yes port=1723 protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 6 - PPTP VPNs" disabled=no new-priority=6 passthrough=yes port=1723 protocol=udp
add action=set-priority chain=prerouting comment="Priority - 6 - SSH" disabled=no new-priority=6 passthrough=yes port=22 protocol=udp
add action=set-priority chain=prerouting comment="Priority - 5 - HTTP Requests" connection-bytes=0-5000000 disabled=no dst-port=80 new-priority=5 passthrough=yes protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 5 - ICQ" disabled=no new-priority=5 passthrough=yes port=5190 protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 5 - Yahoo IM" disabled=no new-priority=5 passthrough=yes port=5050 protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 4 - AOL, IRC" disabled=no new-priority=4 passthrough=yes port=531,5190,6660-6669,6679,6697 protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 4 - AOL, IRC" disabled=no new-priority=4 passthrough=yes port=531 protocol=udp
add action=set-priority chain=prerouting comment="Priority - 4 - Time" disabled=no new-priority=4 passthrough=yes port=37 protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 4 - Time" disabled=no new-priority=4 passthrough=yes port=37,123 protocol=udp
add action=set-priority chain=prerouting comment="Priority - 0 - SFTP" disabled=no dst-port=22 new-priority=0 packet-size=1400-1500 passthrough=yes protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 0 - FTP" disabled=no dst-port=20,21 new-priority=0 packet-size=1400-1500 passthrough=yes protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 0 - HTTP Downloads" connection-bytes=5000000-0 disabled=no new-priority=0 passthrough=yes port=80 protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 0 - Mail Services" disabled=no port=110,995,143,993,25,57,109,465,587 new-priority=0 passthrough=yes protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 0 - SNMP" disabled=no new-priority=0 passthrough=yes port=161,162 protocol=udp
add action=set-priority chain=prerouting comment="Priority - 0 - SNMP" disabled=no new-priority=0 passthrough=yes port=162 protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 0 - IMAP, IMAPS" disabled=no new-priority=0 passthrough=yes port=220,993 protocol=tcp
add action=set-priority chain=prerouting comment="Priority - 0 - IMAP" disabled=no new-priority=0 passthrough=yes port=220 protocol=udp
/
# HTTP,HTTPS,SSH,Telnet,FTP Fix 15/03/2015
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=0.0.0.0/0 dst-port=80 new-connection-mark=WAN1_conn passthrough=yes protocol=tcp comment="HTTP"
add action=mark-packet chain=prerouting disabled=no dst-address=0.0.0.0/0 dst-port=80 in-interface=Local new-packet-mark=QOS_HTTP passthrough=no protocol=tcp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=0.0.0.0/0 dst-port=443 new-connection-mark=WAN1_conn passthrough=yes protocol=tcp comment="HTTPS"
add action=mark-packet chain=prerouting disabled=no dst-address=0.0.0.0/0 dst-port=443 in-interface=Local new-packet-mark=QOS_HTTPS passthrough=no protocol=tcp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=0.0.0.0/0 dst-port=21,22,23 new-connection-mark=WAN1_conn passthrough=yes protocol=tcp comment="SSH,Telnet,FTP"
/
# Cyberdisk Cyberindo
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=0.0.0.0/0 dst-port=8900-8909 new-connection-mark=WAN1_conn passthrough=yes protocol=tcp comment="Cyberdisk Cyberindo"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=0.0.0.0/0 dst-port=8001,21001,22001,9917,20001-20004 new-connection-mark=WAN1_conn passthrough=yes protocol=tcp comment="Cyberdisk AutoUpdate"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=0.0.0.0/0 dst-port=8001,21001,22001,9917,20001-20004 new-connection-mark=WAN1_conn passthrough=yes protocol=udp
/
# IPBonus
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=58.97.46.160 dst-port=80 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="True Digital Plus IP Bonus"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.43.33.80 dst-port=80 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Winner IP Bonus"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.107.140.246 dst-port=80 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="iNi3 NetCafe"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=122.155.167.151 dst-port=80 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="iCT IP Bonus"
/
# Garena # 5GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=111.223.35.0/24 dst-port=8001 new-connection-mark=WAN1_conn passthrough=yes protocol=tcp comment="Auto UpDate Garena"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=111.223.35.0/24 dst-port=8001 new-connection-mark=WAN1_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.117.172.0/24 dst-port=9100,16000,18000,20466,21000-21005 new-connection-mark=WAN1_conn passthrough=yes protocol=tcp comment="Garena Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=111.223.35.0/24 dst-port=30000,18080-18090,40001-41004 new-connection-mark=WAN1_conn passthrough=yes protocol=tcp comment="Talk Talk Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=111.223.35.0/24 dst-port=30000,18080-18090,40001-41004 new-connection-mark=WAN1_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=112.121.158.0/24 dst-port=80 new-connection-mark=WAN1_conn passthrough=yes protocol=tcp comment="HON Shop "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=111.223.35.0/24 dst-port=80 new-connection-mark=WAN1_conn passthrough=yes protocol=tcp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.117.155.0/24 dst-port=9100-9300 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="MS HON "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.117.158.0/24 dst-port=9100-9300 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=111.223.63.0/24 dst-port=11033 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="HON Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=112.121.149.0/24 dst-port=11235-11458 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=112.121.155.0/24 dst-port=11235-11458 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=112.121.156.0/24 dst-port=11235-11458 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.117.158.0/24 dst-port=11235-11458 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=112.121.157.0/24 dst-port=2099,5222,5223,8393-8400 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="LOL Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=173.252.107.0/24 dst-port=2099,5222,5223,8393-8400 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=112.121.157.0/24 dst-port=5000-5500 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=112.121.148.0/24 dst-port=39190-40010 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Point Blank Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=112.121.148.0/24 dst-port=39190-40010 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=111.223.44.0/24 dst-port=6300-6400,7700-7800 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="FIFA Online 3 "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=111.223.44.0/24 dst-port=6300-6400,16300-16340 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=111.223.43.0/24 dst-port=14009-14010 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Lost Saga Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=111.223.43.0/24 dst-port=14009-14010 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# Asiasoft # 17GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=119.46.128.0/24 dst-port=3731-3735 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="8inw Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=61.90.227.0/24 dst-port=10018,18200-18210,18206-18207 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Audition Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.144.223.0/24 dst-port=38101,38111-38122,38151-38152,63111-63122 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Cabal Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.4.158.0/24 dst-port=7775-7786,11000-24999,31333 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="DC Universe Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.4.156.0/24 dst-port=14300,14400-14406,14500-14600 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Dragon Nest Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.4.156.0/24 dst-port=15100-15200 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.4.157.0/24 dst-port=9100,9300,9301,9400 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Elsword Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.4.157.0/24 dst-port=9101,9301 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=119.46.249.0/24 dst-port=8465,8468 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="FC Manager "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.144.179.0/24 dst-port=2000,7000-7030 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Granado Espada "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.4.158.0/24 dst-port=12000-12999 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="PHANTASY STAR ONLINE 2 "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.4.156.0/24 dst-port=5000,6800,6900,7000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Ragnarok Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.4.157.0/24 dst-port=7101,7201-7209,7401-7403 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Ragnarok II Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.4.157.0/24 dst-port=7101,7201-7209,7401-7403 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=119.46.129.0/24 dst-port=443,16666-16668,28000,28002,28008,28012,28013 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="S4 League Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=119.46.129.0/24 dst-port=38912-40912 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=108.168.200.0/24 dst-port=7031-7040 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Strife Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=207.244.69.0/24 dst-port=11235-11335 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=85.17.150.0/24 dst-port=11235-11335 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=207.244.69.0/24 dst-port=7335-7355 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=207.244.69.0/24 dst-port=7335-7355 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.144.130.0/24 dst-port=12000-12001,15000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Sudden attact Online"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.144.130.0/24 dst-port=27000-28000 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.144.166.0/24 dst-port=30010,30020,30030,30040,30050,30060 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Ultimate Heroes Battle "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.144.166.0/24 dst-port=50000 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.144.179.0/24 dst-port=15000-15001,16000-16151 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Yulgang Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.4.157.0/24 dst-port=15000-15030 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Yulgang II"
/
# True Digital Plus # 7GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=61.91.68.0/24 dst-port=12567,11000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="EOS Online"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=61.90.203.0/24 dst-port=20000-21000,27930-27950 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Special Force"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=61.90.203.0/24 dst-port=20000-21000,27935 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=61.91.229.0/24 dst-port=3724 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Magic World II"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=58.97.46.0/24 dst-port=2002,2201-2210,4001 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Tao Yuan"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=61.91.69.0/24 dst-port=16021,16101,16201-16220 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Love Beat"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=61.91.69.0/24 dst-port=8400,8200,8800 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="LOE Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=58.97.80.0/26 dst-port=7000-8000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="The King of Fighters"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=58.97.80.0/26 dst-port=20000-39999 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# Ini3 # 7GAME TP+PORT Update 10/03/2558
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.195.98.0/24 dst-port=3000,4000,20100,20200,20300,20900 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="GunZ2 Thailand "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.195.98.0/24 dst-port=7001-65535 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.107.140.0/24 dst-port=5184,10188 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Pirate Force"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.107.140.0/24 dst-port=10000-50000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Divine Warriors"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.107.140.0/24 dst-port=11101,11054 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="GranAge"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.107.140.0/24 dst-port=11910-12910 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.107.140.0/24 dst-port=10501-10600,10711-10715,10721 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="C9 Thailand "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.107.140.0/24 dst-port=10711-10760 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.107.140.0/24 dst-port=8090,10100-10105,20200-20205 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Pangya"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.195.98.0/24 dst-port=15400,23000,28000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Flyff"
/
# Winner # 9GAME TP+PORT Update 10/03/2558
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.43.38.0/24 dst-port=20000-40000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="FEAR Online"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.43.38.0/24 dst-port=20000-40000 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.43.38.0/24 dst-port=11002-11014,12100,12111 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="FOX Online"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.43.39.0/24 dst-port=10007,10009,10020 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Priston Tale Online"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.43.38.0/24 dst-port=4200,6000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Draco Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.43.38.0/24 dst-port=18008 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="DayBreak Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.43.39.0/24 dst-port=5567-5570,6543-6546,10021-10025 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Fantasy Frontier,LH Online"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.43.34.0/24 dst-port=7341-7350,7451,8421 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="X-SHOT"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.43.34.0/24 dst-port=7777-7876,30000-30100 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.43.35.0/24 dst-port=1818 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Seal Online "
/
# TOT Online # 2GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=180.180.247.0/24 dst-port=9000-10000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="TalesRunner Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=180.180.247.0/24 dst-port=9000-10000 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.113.10.0/24 dst-port=13000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="ToyWars "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.113.10.0/24 dst-port=39000 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# Digicarft # 3GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=210.86.180.0/24 dst-port=13400-13450 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Getamped "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=210.86.180.0/24 dst-port=7000-7200 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Getamped2 "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=210.86.180.0/24 dst-port=7000-7200 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=210.86.180.0/24 dst-port=23456-23458 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="CosmicBreak "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=210.86.180.0/24 dst-port=23456-23458 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# Golden Soft # 2GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=119.46.96.0/24 dst-port=29990-30100 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Zone4 Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=119.46.96.0/24 dst-port=29990-30100 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=119.46.96.0/24 dst-port=5001-5099,9001-9099,9601-9699,9701-9799 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="SDGO Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=119.46.96.0/24 dst-port=6001-6099,10001-20000 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# Jaya # 2GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.43.36.0/24 dst-port=14400-14700,16400-16605 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Titan DarkStory Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.43.36.0/24 dst-port=14800-15800 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Luna Online"
/
# Game World # 3GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.183.192.0/24 dst-port=4100-4200 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="laghaim "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.183.192.0/24 dst-port=4100-4200 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.183.192.0/24 dst-port=4000-4050 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="LastChaos "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.146.250.0/24 dst-port=15100-15600 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="operation7 "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.146.250.0/24 dst-port=15100-15600 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# Cubinet # 5GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.45.0/24 dst-port=2001-2004 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="9yin "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.45.0/24 dst-port=9500,9505,9510-9515 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="avatar star "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.45.146 dst-port=29000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Zhuxian "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.45.146 dst-port=29000 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.45.130 dst-port=29000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Perfect world "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.45.130 dst-port=29000 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=110.74.178.0/24 dst-port=9000-9500 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Final Combat "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=110.74.178.0/24 dst-port=9000-9500 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# Onenet # 2GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.29.108.0/24 dst-port=5000-5200 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Gulong "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.29.108.0/24 dst-port=5000-5200 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# i Digital Connect # 4GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.39.0/24 dst-port=7716,6688 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="TS3 SAGA "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.39.0/24 dst-port=7716,6688 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.32.0/24 dst-port=5000-5500 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="12Tails Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.32.0/24 dst-port=5000-5500 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.39.0/24 dst-port=16000-16500 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Dragon’s Prophet "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.39.0/24 dst-port=16000-16500 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.29.108.0/24 dst-port=14001-14010 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Blast Breaker "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.29.108.0/24 dst-port=14001-14010 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# Netmarble # 1GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.55.0/24 dst-port=28900-28999 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="EverybodyMarble"
/
# Xinxere # 1GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.142.207.0/24 dst-port=5000-5600 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="RAN IN TH"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.142.207.0/24 dst-port=5000-5600 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# NJoy # 2GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.82.0/24 dst-port=9223 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Swordsman"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.82.0/24 dst-port=9223 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.82.0/24 dst-port=29000-29011 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Saint Seiya"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.82.0/24 dst-port=29000-29011 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# ClickAlot # 1GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.170.249.0/24 dst-port=9900-9903 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="FinalBullet"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=27.254.94.0/24 dst-port=9000,9900-9903 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp
/
# Infinity 999 # 1GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=122.155.187.0/24 dst-port=3100-3103,3818-3825 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Heroes of Kingdoms"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=122.155.187.0/24 dst-port=3100-3103,3818-3825 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# Electronic Extream # 1 GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.41.59.0/24 dst-port=34000-35000 new-connection-mark=WAN2_conn passthrough=yes protocol=udp comment="Infestation Thailand"
/
#### Battle # 2GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=202.9.66.0/24 dst-port=1119 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="StarCraft II"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.77.189.0/24 dst-port=1119 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.77.189.0/24 dst-port=6113,1119,53336,39110 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=12.130.244.0/24 dst-port=1119,6881-6999 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="Diablo III"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=12.130.245.0/24 dst-port=6120,6881-6999 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# Wargaming # 1GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=92.223.16.0/24 dst-port=20013-20018 new-connection-mark=WAN2_conn passthrough=yes protocol=udp comment="World of Tanks "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=92.223.16.0/24 dst-port=32801-32825 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
/
# TCG 2GAME
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=61.91.127.194 dst-port=3000-65000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="TCG Network"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=61.19.241.41 dst-port=3000-65000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=210.86.182.0/24 dst-port=3000-65000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=124.120.199.0/24 dst-port=3000-65000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=122.155.12.0/24 dst-port=3000-65000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=203.144.224.0/24 dst-port=3000-65000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp
/
# STEAM-DotA 2
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=146.66.152.0/24 dst-port=27000-27030 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="STEAM-DotA 2 Server Europe"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=146.66.152.0/24 dst-port=29000-29020 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.10.124.0/24 dst-port=27000-28999 new-connection-mark=WAN2_conn passthrough=yes protocol=udp comment="STEAM-DotA 2 Server SEA"
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=103.28.54.0/24 dst-port=27000-28999 new-connection-mark=WAN2_conn passthrough=yes protocol=udp
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=173.192.105.0/24 dst-port=11031-12000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp comment="HON Inter Online "
add action=mark-connection chain=prerouting disabled=no in-interface=Local dst-address=96.127.149.0/24 dst-port=11031-12000 new-connection-mark=WAN2_conn passthrough=yes protocol=tcp
/
#
/ip firewall mangle
add chain=prerouting connection-mark=WAN1_conn in-interface=Local action=mark-routing new-routing-mark=to_WAN1
add chain=prerouting connection-mark=WAN2_conn in-interface=Local action=mark-routing new-routing-mark=to_WAN2
/
# Route
/ip route
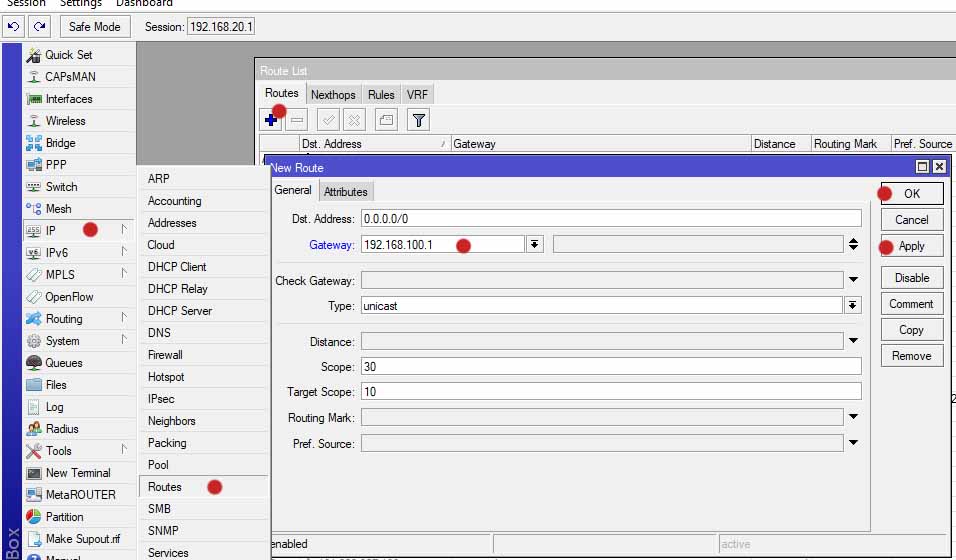
add dst-address=0.0.0.0/0 distance=1 gateway=192.168.1.1 routing-mark=to_WAN1 check-gateway=ping comment=WAN1
add dst-address=0.0.0.0/0 distance=1 gateway=192.168.2.1 routing-mark=to_WAN2 check-gateway=ping comment=WAN2
add dst-address=0.0.0.0/0 distance=2 gateway=192.168.1.1 routing-mark=to_WAN2 check-gateway=ping
add dst-address=0.0.0.0/0 distance=2 gateway=192.168.2.1 routing-mark=to_WAN1 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=192.168.1.1,192.168.2.1 distance=1 check-gateway=ping comment=WAN1
add dst-address=0.0.0.0/0 gateway=192.168.2.1,192.168.1.1 distance=2 check-gateway=ping comment=WAN2
/
# Nat
/ip firewall nat
add chain=srcnat out-interface=WAN1 action=masquerade
add chain=srcnat out-interface=WAN2 action=masquerade
/
# IP Public Dota Fix 16/03/2015(D/M/Y)
/ip firewall nat
add action=src-nat chain=srcnat dst-address=192.168.10.11 dst-port=6101 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6101"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6101 protocol=tcp to-addresses=192.168.10.11 to-ports=6101
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6101 protocol=tcp to-addresses=192.168.10.11 to-ports=6101 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.12 dst-port=6102 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6102"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6102 protocol=tcp to-addresses=192.168.10.12 to-ports=6102
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6102 protocol=tcp to-addresses=192.168.10.12 to-ports=6102 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.13 dst-port=6103 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6103"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6103 protocol=tcp to-addresses=192.168.10.13 to-ports=6103
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6103 protocol=tcp to-addresses=192.168.10.13 to-ports=6103 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.14 dst-port=6104 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6104"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6104 protocol=tcp to-addresses=192.168.10.14 to-ports=6104
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6104 protocol=tcp to-addresses=192.168.10.14 to-ports=6104 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.15 dst-port=6105 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6105"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6105 protocol=tcp to-addresses=192.168.10.15 to-ports=6105
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6105 protocol=tcp to-addresses=192.168.10.15 to-ports=6105 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.16 dst-port=6106 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6106"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6106 protocol=tcp to-addresses=192.168.10.16 to-ports=6106
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6106 protocol=tcp to-addresses=192.168.10.16 to-ports=6106 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.17 dst-port=6107 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6107"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6107 protocol=tcp to-addresses=192.168.10.17 to-ports=6107
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6107 protocol=tcp to-addresses=192.168.10.17 to-ports=6107 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.18 dst-port=6108 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6108"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6108 protocol=tcp to-addresses=192.168.10.18 to-ports=6108
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6108 protocol=tcp to-addresses=192.168.10.18 to-ports=6108 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.19 dst-port=6109 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6109"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6109 protocol=tcp to-addresses=192.168.10.19 to-ports=6109
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6109 protocol=tcp to-addresses=192.168.10.19 to-ports=6109 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.20 dst-port=6110 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6110"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6110 protocol=tcp to-addresses=192.168.10.20 to-ports=6110
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6110 protocol=tcp to-addresses=192.168.10.20 to-ports=6110 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.21 dst-port=6111 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6111"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6111 protocol=tcp to-addresses=192.168.10.21 to-ports=6111
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6111 protocol=tcp to-addresses=192.168.10.21 to-ports=6111 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.22 dst-port=6112 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6112"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6112 protocol=tcp to-addresses=192.168.10.22 to-ports=6112
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6112 protocol=tcp to-addresses=192.168.10.22 to-ports=6112 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.23 dst-port=6113 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6113"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6113 protocol=tcp to-addresses=192.168.10.23 to-ports=6113
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6113 protocol=tcp to-addresses=192.168.10.23 to-ports=6113 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.24 dst-port=6114 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6114"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6114 protocol=tcp to-addresses=192.168.10.24 to-ports=6114
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6114 protocol=tcp to-addresses=192.168.10.24 to-ports=6114 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.25 dst-port=6115 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6115"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6115 protocol=tcp to-addresses=192.168.10.25 to-ports=6115
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6115 protocol=tcp to-addresses=192.168.10.25 to-ports=6115 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.26 dst-port=6116 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6116"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6116 protocol=tcp to-addresses=192.168.10.26 to-ports=6116
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6116 protocol=tcp to-addresses=192.168.10.26 to-ports=6116 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.27 dst-port=6117 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6117"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6117 protocol=tcp to-addresses=192.168.10.27 to-ports=6117
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6117 protocol=tcp to-addresses=192.168.10.27 to-ports=6117 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.28 dst-port=6118 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6118"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6118 protocol=tcp to-addresses=192.168.10.28 to-ports=6118
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6118 protocol=tcp to-addresses=192.168.10.28 to-ports=6118 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.29 dst-port=6119 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6119"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6119 protocol=tcp to-addresses=192.168.10.29 to-ports=6119
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6119 protocol=tcp to-addresses=192.168.10.29 to-ports=6119 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.30 dst-port=6120 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6120"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6120 protocol=tcp to-addresses=192.168.10.30 to-ports=6120
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6120 protocol=tcp to-addresses=192.168.10.30 to-ports=6120 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.31 dst-port=6121 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6121"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6121 protocol=tcp to-addresses=192.168.10.31 to-ports=6121
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6121 protocol=tcp to-addresses=192.168.10.31 to-ports=6121 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.32 dst-port=6122 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6122"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6122 protocol=tcp to-addresses=192.168.10.32 to-ports=6122
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6122 protocol=tcp to-addresses=192.168.10.32 to-ports=6122 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.33 dst-port=6123 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6123"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6123 protocol=tcp to-addresses=192.168.10.33 to-ports=6123
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6123 protocol=tcp to-addresses=192.168.10.33 to-ports=6123 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.34 dst-port=6124 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6124"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6124 protocol=tcp to-addresses=192.168.10.34 to-ports=6124
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6124 protocol=tcp to-addresses=192.168.10.34 to-ports=6124 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.35 dst-port=6125 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6125"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6125 protocol=tcp to-addresses=192.168.10.35 to-ports=6125
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6125 protocol=tcp to-addresses=192.168.10.35 to-ports=6125 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.36 dst-port=6126 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6126"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6126 protocol=tcp to-addresses=192.168.10.36 to-ports=6126
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6126 protocol=tcp to-addresses=192.168.10.36 to-ports=6126 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.37 dst-port=6127 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6127"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6127 protocol=tcp to-addresses=192.168.10.37 to-ports=6127
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6127 protocol=tcp to-addresses=192.168.10.37 to-ports=6127 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.38 dst-port=6128 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6128"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6128 protocol=tcp to-addresses=192.168.10.38 to-ports=6128
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6128 protocol=tcp to-addresses=192.168.10.38 to-ports=6128 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.39 dst-port=6129 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6129"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6129 protocol=tcp to-addresses=192.168.10.39 to-ports=6129
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6129 protocol=tcp to-addresses=192.168.10.39 to-ports=6129 in-interface=!WAN2
add action=src-nat chain=srcnat dst-address=192.168.10.40 dst-port=6130 protocol=tcp src-address=192.168.10.0/24 to-addresses=192.168.10.1 comment="IP Public Dota - 6130"
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6130 protocol=tcp to-addresses=192.168.10.40 to-ports=6130
add action=dst-nat chain=dstnat dst-address-type=local dst-port=6130 protocol=tcp to-addresses=192.168.10.40 to-ports=6130 in-interface=!WAN2
/
/ip firewall mangle
add action=accept chain=prerouting src-port=6101-6130 protocol=tcp passthrough=no comment="IP Public Dota 6101 - 6130"
add action=accept chain=prerouting dst-port=6101-6130 protocol=tcp passthrough=no
/
# CCTV = IP CCTP 192.168.10.5 Port 8181
/ip firewall nat
add action=dst-nat chain=dstnat dst-address-type=local dst-port=8080 protocol=tcp to-addresses=192.168.10.5 to-ports=8080 comment="CCTV Server"
/
# DHCP Server
/ip pool add name=default-dhcp ranges=192.168.10.10-192.168.10.200
/
/ip dhcp-server add name=default address-pool=default-dhcp interface=Local disabled=no
/
/ip dhcp-server network add address=192.168.10.0/24 gateway=192.168.10.1 dns-server=192.168.10.1 comment="default configuration"
/
# DNS Server memilih DNS untuk mencocokkan Internet Service Provider
# 203.144.207.29,203.144.207.49 True DNS
# 110.164.252.138,110.164.252.139 3BB DNS
# 110.164.252.222,110.164.252.223 BB DNS
# 61.19.245.245,61.19.245.246 CAT ONNET DNS
# 61.19.253.134,61.19.253.136 CAT ONNET DNS
# 61.19.254.134,61.19.254.135 CAT ONNET DNS
# 61.19.255.134,61.19.255.135 CAT ONNET DNS
# 8.8.8.8,8.8.4.4 Google DNS
/ip dns
set allow-remote-requests=yes cache-max-ttl=1w cache-size=5000K max-udp-packet-size=512 servers=8.8.8.8,8.8.4.4
/
# NTP Server
/system clock
set time-zone-name=Asia/Bangkok
/
/system ntp client
set enabled=yes mode=unicast primary-ntp=203.185.67.115 secondary-ntp=203.185.67.115
/
# Service
/ip service
set telnet disabled=yes
set ftp disabled=yes
set ssh disabled=no
set api disabled=no
/
# Bruteforce login SSH
/ip firewall filter
add chain=input action=jump jump-target=Brute protocol=tcp dst-port=22 comment="Check Brute" disabled=no
add chain=Brute protocol=tcp dst-port=22 connection-state=new src-address-list=safe action=accept comment="Allow SSH safe hosts" disabled=no
add chain=Brute protocol=tcp dst-port=22 connection-state=new src-address-list=ssh_stage3 action=add-src-to-address-list address-list=ssh_blacklist address-list-timeout=10d comment="SSH brute forcers blacklisting" disabled=no
add chain=Brute protocol=tcp dst-port=22 connection-state=new src-address-list=ssh_stage2 action=add-src-to-address-list address-list=ssh_stage3 address-list-timeout=1m comment="SSH brute forcers the third stage" disabled=no
add chain=Brute protocol=tcp dst-port=22 connection-state=new src-address-list=ssh_stage1 action=add-src-to-address-list address-list=ssh_stage2 address-list-timeout=1m comment="SSH brute forcers the second stage" disabled=no
add chain=Brute protocol=tcp dst-port=22 connection-state=new action=add-src-to-address-list address-list=ssh_stage1 address-list-timeout=1m comment="SSH brute forcers the first stage" disabled=no
add chain=Brute protocol=tcp dst-port=22 src-address-list=ssh_blacklist action=drop comment="Drop SSH brute forcers" disabled=no
/
# Bruteforce login Winbox
/ip firewall filter
add chain=input action=jump jump-target=Brute protocol=tcp dst-port=8291 comment="Check Brute" disabled=no
add chain=Brute protocol=tcp dst-port=8291 connection-state=new src-address-list=safe action=accept comment="Allow WinBox safe hosts" disabled=no
add chain=Brute protocol=tcp dst-port=8291 connection-state=new src-address-list=wb_stage3 action=add-src-to-address-list address-list=wb_blacklist address-list-timeout=10d comment="WinBox brute forcers blacklisting" disabled=no
add chain=Brute protocol=tcp dst-port=8291 connection-state=new src-address-list=wb_stage2 action=add-src-to-address-list address-list=wb_stage3 address-list-timeout=1m comment="WinBox brute forcers the third stage" disabled=no
add chain=Brute protocol=tcp dst-port=8291 connection-state=new src-address-list=wb_stage1 action=add-src-to-address-list address-list=wb_stage2 address-list-timeout=1m comment="WinBox brute forcers the second stage" disabled=no
add chain=Brute protocol=tcp dst-port=8291 connection-state=new action=add-src-to-address-list address-list=wb_stage1 address-list-timeout=1m comment="WinBox brute forcers the first stage" disabled=no
add chain=Brute protocol=tcp dst-port=8291 src-address-list=wb_blacklist action=drop comment="Drop WinBox brute forcers" disabled=no
/
# Block Port Scaner
/ip firewall filter
add chain=input protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list address-list="port_scanners" address-list-timeout=2w comment="PORTSCAN Port scanners to list " disabled=no
add chain=input protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list="port_scanners" address-list-timeout=2w comment="PORTSCAN NMAP FIN Stealth scan"
add chain=input protocol=tcp tcp-flags=fin,syn action=add-src-to-address-list address-list="port_scanners" address-list-timeout=2w comment="PORTSCAN SYN/FIN scan"
add chain=input protocol=tcp tcp-flags=syn,rst action=add-src-to-address-list address-list="port_scanners" address-list-timeout=2w comment="PORTSCAN SYN/RST scan"
add chain=input protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack action=add-src-to-address-list address-list="port_scanners" address-list-timeout=2w comment="PORTSCAN FIN/PSH/URG scan"
add chain=input protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg action=add-src-to-address-list address-list="port_scanners" address-list-timeout=2w comment="PORTSCAN ALL/ALL scan"
add chain=input protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list="port_scanners" address-list-timeout=2w comment="PORTSCAN NMAP NULL scan"
add chain=input src-address-list="port_scanners" action=drop comment="PORTSCAN dropping port scanners" disabled=no
/
# DNS Attack Prevention Fix 10/03/2015(D/M/Y)
/ip firewall address-list
add address=192.168.0.0/16 list=DNS_Accept
add address=203.144.207.29 list=DNS_Accept comment="True DNS Server"
add address=203.144.207.49 list=DNS_Accept comment="True DNS Server"
add address=110.164.252.138 list=DNS_Accept comment="3BB DNS Server"
add address=110.164.252.139 list=DNS_Accept comment="3BB DNS Server"
add address=110.164.252.222 list=DNS_Accept comment="3BB DNS Server"
add address=110.164.252.223 list=DNS_Accept comment="3BB DNS Server"
add address=202.129.27.133 list=DNS_Accept comment="CAT ONNET Server"
add address=61.19.245.245 list=DNS_Accept comment="CAT ONNET Server"
add address=61.19.245.246 list=DNS_Accept comment="CAT ONNET Server"
add address=61.19.253.134 list=DNS_Accept comment="CAT ONNET Server"
add address=61.19.253.136 list=DNS_Accept comment="CAT ONNET Server"
add address=61.19.254.134 list=DNS_Accept comment="CAT ONNET Server"
add address=61.19.254.135 list=DNS_Accept comment="CAT ONNET Server"
add address=61.19.255.134 list=DNS_Accept comment="CAT ONNET Server"
add address=61.19.255.135 list=DNS_Accept comment="CAT ONNET Server"
add address=8.8.8.8/32 list=DNS_Accept comment="Google DNS Server"
add address=8.8.4.4/32 list=DNS_Accept comment="Google DNS Server"
add address=4.2.2.1/32 list=DNS_Accept comment="GTEI DNS Server"
add address=4.2.2.2/32 list=DNS_Accept comment="GTEI DNS Server"
add address=4.2.2.3/32 list=DNS_Accept comment="GTEI DNS Server"
add address=4.2.2.4/32 list=DNS_Accept comment="GTEI DNS Server"
add address=4.2.2.5/32 list=DNS_Accept comment="GTEI DNS Server"
add address=4.2.2.6/32 list=DNS_Accept comment="GTEI DNS Server"
/
/ip firewall filter
add action=jump chain=input disabled=no jump-target=DNS_DDoS comment="Jump to DNS_DDoS Chain"
add action=accept chain=DNS_DDoS disabled=no port=53 protocol=tcp src-address-list=DNS_Accept comment="Make exceptions for DNS"
add action=accept chain=DNS_DDoS disabled=no dst-address-list=DNS_Accept port=53 protocol=tcp
add action=accept chain=DNS_DDoS disabled=no port=53 protocol=udp src-address-list=DNS_Accept
add action=accept chain=DNS_DDoS disabled=no dst-address-list=DNS_Accept port=53 protocol=udp
add action=add-src-to-address-list address-list=DNS_DDoS chain=DNS_DDoS address-list-timeout=5m disabled=no port=53 protocol=tcp src-address-list=!DNS_Accept comment="Add DNS_DDoS Offenders to Blacklist"
add action=add-src-to-address-list address-list=DNS_DDoS chain=DNS_DDoS address-list-timeout=5m disabled=no port=53 protocol=udp src-address-list=!DNS_Accept
add action=drop chain=DNS_DDoS disabled=no src-address-list=DNS_DDoS comment="Drop DNS_DDoS Offenders"
add action=return chain=DNS_DDoS disabled=no comment="Return from DNS_DDoS Chain"
/
# Block Flood Ping
/ip firewall filter
add chain=input protocol=icmp limit=50/5s,2 comment="Allow limited pings"
add chain=input protocol=icmp action=drop comment="Drop excess pings"
/
# Block UltraSurf
/ip firewall address-list
add address=65.49.0.0/17 disabled=no list=UltraSurf
add address=204.107.140.0/24 disabled=no list=UltraSurf
/
/ip firewall mangle
add action=add-src-to-address-list address-list=UltraSurfUsers address-list-timeout=5m chain=prerouting comment="Block UltraSurf" disabled=no dst-address-list=UltraSurf dst-port=443 protocol=tcp
/
/ip firewall filter
add action=drop chain=forward comment="Block UltraSurf" disabled=no dst-port=443 protocol=tcp src-address-list=UltraSurfUsers
/
# Block Hotspot Shield
/ip firewall address-list
add address=157.56.106.0/24 disabled=no list=Hotspotshield_ZaiB
add address=157.56.144.0/24 disabled=no list=Hotspotshield_ZaiB
add address=198.144.116.0/24 disabled=no list=Hotspotshield_ZaiB
add address=204.14.77.0/24 disabled=no list=Hotspotshield_ZaiB
add address=204.14.0.0/16 disabled=no list=Hotspotshield_ZaiB
add address=205.164.34.0/24 disabled=no list=Hotspotshield_ZaiB
add address=209.73.0.0/16 disabled=no list=Hotspotshield_ZaiB
add address=212.118.232.0/24 disabled=no list=Hotspotshield_ZaiB
add address=216.172.138.0/24 disabled=no list=Hotspotshield_ZaiB
add address=216.172.0.0/16 disabled=no list=Hotspotshield_ZaiB
add address=46.0.0.0/8 disabled=no list=Hotspotshield_ZaiB
add address=66.171.229.0/24 disabled=no list=Hotspotshield_ZaiB
add address=68.68.107.0/24 disabled=no list=Hotspotshield_ZaiB
add address=68.68.108.0/24 disabled=no list=Hotspotshield_ZaiB
add address=69.22.168.0/24 disabled=no list=Hotspotshield_ZaiB
add address=69.22.170.0/24 disabled=no list=Hotspotshield_ZaiB
add address=74.115.0.0/16 disabled=no list=Hotspotshield_ZaiB
add address=94.245.121.0/24 disabled=no list=Hotspotshield_ZaiB
add address=69.22.185.0/24 disabled=no list=Hotspotshield_ZaiB
add address=174.129.0.0/16 disabled=no list=Hotspotshield_ZaiB
add address=216.172.135.0/24 disabled=no list=Hotspotshield_ZaiB
add address=67.220.0.0/16 disabled=no list=Hotspotshield_ZaiB
add address=50.0.0.0/8 disabled=no list=Hotspotshield_ZaiB
add address=79.125.0.0/16 disabled=no list=Hotspotshield_ZaiB
add address=75.101.0.0/16 disabled=no list=Hotspotshield_ZaiB
add address=176.56.0.0/16 disabled=no list=Hotspotshield_ZaiB
add address=54.75.0.0/16 disabled=no list=Hotspotshield_ZaiB
add address=54.161.0.0/16 disabled=no list=Hotspotshield_ZaiB
add address=199.188.0.0/16 disabled=no list=Hotspotshield_ZaiB
/
/ip firewall filter
add action=drop chain=forward disabled=no src-address-list=Hotspotshield_ZaiB comment="Block Hotspot Shield Addresses"
add action=drop chain=forward disabled=no dst-port=990,179,105,706,5245,3451,15009 protocol=tcp comment="Block Hotspot Shield Ports"
/
# Block PSP&Torrent
/ip firewall filter
add action=drop chain=forward in-interface=!WAN1 dst-address-list=Torrent disabled=no comment="Block PSP&Torrent No.0 : WAN1-WAN2"
add action=drop chain=forward in-interface=!WAN2 dst-address-list=Torrent disabled=no
add action=add-dst-to-address-list address-list=Torrent chain=forward address-list-timeout=5m p2p=all-p2p in-interface=Local comment="Block PSP&Torrent No.1 : Classic non security torrent"
add action=add-dst-to-address-list address-list=Torrent chain=forward address-list-timeout=5m content=d1:ad2:id20: dst-port=1025-65535 in-interface=Local packet-size=95-190 protocol=udp comment="Block PSP&Torrent No.2 : Outgoing DHT"
add action=add-dst-to-address-list address-list=Torrent chain=forward address-list-timeout=5m content="info_hash=" dst-port=2710,80 in-interface=Local protocol=tcp comment="Block PSP&Torrent No.3 : Outgoing TCP announce"
add action=add-dst-to-address-list address-list=Torrent chain=forward address-list-timeout=5m content="\r\nInfohash:" dst-port=6771 in-interface=Local protocol=udp comment="Block PSP&Torrent No.4 : Broadcast"
add action=drop chain=forward in-interface=Local content=.torrent dst-port=80 protocol=tcp comment="Block PSP&Torrent No.5 : Drop all Download .torrent Files"
add action=drop chain=forward in-interface=Local dst-address-list=Torrent comment="Block PSP&Torrent No.6 : Drop all Torrent Connection"
/
# Block WEB&DNS Torrent
/ip firewall layer7-protocol
add name=L7_WEB_Torrent regexp="^.*(get|GET).+(tang-mo|bitded|thailandtorrent|siambit|unlimitz|smilebit|zbeasy|naze-bit|rmbit|bit24hrs|ikkyonline|bit-th|inwdrama|cupidtorrent|playonbit|gaythaitorrent|nonamebit|nongpink|kickass).*\$"
add name=L7_DNS_Torrent regexp="^.+(tang-mo|bitded|thailandtorrent|siambit|unlimitz|smilebit|zbeasy|naze-bit|rmbit|bit24hrs|ikkyonline|bit-th|inwdrama|cupidtorrent|playonbit|gaythaitorrent|nonamebit|nongpink|kickass).*\$"
/
/ip firewall filter
add action=drop chain=forward in-interface=!WAN1 dst-address-list=Torrent_Web disabled=no comment="Block WEB&DNS Torrent No.0 : WAN1-WAN2"
add action=drop chain=forward in-interface=!WAN1 dst-address-list=Torrent_Dns disabled=no
add action=drop chain=forward in-interface=!WAN2 dst-address-list=Torrent_Web disabled=no
add action=drop chain=forward in-interface=!WAN2 dst-address-list=Torrent_Dns disabled=no
add action=add-dst-to-address-list chain=forward address-list=Torrent_Web address-list-timeout=5m layer7-protocol=L7_WEB_Torrent disabled=no in-interface=Local comment="Block WEB&DNS Torrent No.1 : Forward WEB"
add action=add-dst-to-address-list chain=forward address-list=Torrent_Dns address-list-timeout=5m layer7-protocol=L7_DNS_Torrent disabled=no in-interface=Local comment="Block WEB&DNS Torrent No.2 : Forward DNS"
add action=drop chain=forward in-interface=Local dst-address-list=Torrent_Web disabled=no comment="Block WEB&DNS Torrent No.3 : Drop Web Connection"
add action=drop chain=forward in-interface=Local dst-address-list=Torrent_Dns disabled=no comment="Block WEB&DNS Torrent No.4 : Drop Dns Connection"
/
# Block WEB&DNS ProGame
/ip firewall layer7-protocol
add name=L7_WEB_ProGame regexp="^.*(get|GET).+(trr-pro|progamesmon|progamesbpt|isiontaohackpro|profree|dotathaigg|ro69mcskv|g99network|pbprojectv99|theprozohot|KrubWalHacker|mamposthz.com|auavc.net|Dotathaiggv2|probotfree|pro108|dmprozone|getprobot).*\$"
add name=L7_DNS_ProGame regexp="^.+(trr-pro|progamesmon|progamesbpt|isiontaohackpro|profree|dotathaigg|ro69mcskv|g99network|pbprojectv99|theprozohot|KrubWalHacker|mamposthz.com|auavc.net|Dotathaiggv2|probotfree|pro108|dmprozone|getprobot).*\$"
/
/ip firewall filter
add action=drop chain=forward in-interface=!WAN1 dst-address-list=ProGame_Web disabled=no comment="Block WEB&DNS ProGame No.0 : WAN1-WAN2"
add action=drop chain=forward in-interface=!WAN1 dst-address-list=ProGame_Dns disabled=no
add action=drop chain=forward in-interface=!WAN2 dst-address-list=ProGame_Web disabled=no
add action=drop chain=forward in-interface=!WAN2 dst-address-list=ProGame_Dns disabled=no
add action=add-dst-to-address-list chain=forward address-list=ProGame_Web address-list-timeout=5m layer7-protocol=L7_WEB_ProGame disabled=no in-interface=Local comment="Block WEB&DNS ProGame No.1 : Forward WEB"
add action=add-dst-to-address-list chain=forward address-list=ProGame_Dns address-list-timeout=5m layer7-protocol=L7_DNS_ProGame disabled=no in-interface=Local comment="Block WEB&DNS ProGame No.2 : Forward DNS"
add action=drop chain=forward in-interface=Local dst-address-list=ProGame_Web disabled=no comment="Block WEB&DNS ProGame No.3 : Drop Web Connection"
add action=drop chain=forward in-interface=Local dst-address-list=ProGame_Dns disabled=no comment="Block WEB&DNS ProGame No.4 : Drop Dns Connection"
/
# Block Baidu
/ip firewall layer7-protocol
add name=L7_Baidu regexp="^.+(baidu.com|baidu|imobile.baidu.com|555.in.th|hao123.cn|baidu.co.th|jp.hao123.wshifen.com|translate.baidu.co.th|mx.n.shifen.com|ns1.softlayer.com|ns2.softlayer.com|dl-vip.pcfaceter.baidu.co.th|download.antivirus.baidu.com|rtp.bav.baidu.com|th.browser.baidu.com|browser0.wshifen.com|bavhome.wshifen.com|security.baidu.co.th|www.pcfaster.com|pcfaster|antivirus.baidu.com|pcfhome.wshifen.com|dns.baidu.com|ns1.baidu.com|ns2.baidu.com|ns3.baidu.com|ns4.baidu.com|ns7.baidu.com|jpmx.baidu.com|mx1.baidu.com|mx50.baidu.com|hk.hao123.wshifen.com|hao123.com|hao123|ns.hao123.com|th.hao123.com|eg.hao123.com|en.hao123.com|antivirus.baidu.co.th).*\$"
/
/ip firewall address-list
add address=192.168.10.0/24 list=Local
/
/ip firewall filter
add action=add-dst-to-address-list address-list=Baidu address-list-timeout=5m chain=forward dst-address-list=!Local layer7-protocol=L7_Baidu comment="Block Baidu"
add action=drop chain=forward dst-address-list=Baidu src-address-list=Local
/
# Block Virus
add action=jump chain=input comment="Jump to Virus Chain" disabled=no jump-target=Virus
add action=drop chain=Virus comment="Drop Blaster Worm" disabled=no dst-port=135-139 protocol=tcp
add action=drop chain=Virus comment="Drop Blaster Worm" disabled=no dst-port=445 protocol=tcp
add action=drop chain=Virus comment="Drop Blaster Worm" disabled=no dst-port=445 protocol=udp
add action=drop chain=Virus comment="Drop Messenger Worm" disabled=no dst-port=135-139 protocol=udp
add action=drop chain=Virus comment=Conficker disabled=no dst-port=593 protocol=tcp
add action=drop chain=Virus comment=Worm disabled=no dst-port=1024-1030 protocol=tcp
add action=drop chain=Virus comment="ndm requester" disabled=no dst-port=1363 protocol=tcp
add action=drop chain=Virus comment="ndm server" disabled=no dst-port=1364 protocol=tcp
add action=drop chain=Virus comment="screen cast" disabled=no dst-port=1368 protocol=tcp
add action=drop chain=Virus comment=hromgrafx disabled=no dst-port=1373 protocol=tcp
add action=drop chain=Virus comment="Drop MyDoom" disabled=no dst-port=1080 protocol=tcp
add action=drop chain=Virus comment=cichlid disabled=no dst-port=1377 protocol=tcp
add action=drop chain=Virus comment=Worm disabled=no dst-port=1433-1434 protocol=tcp
add action=drop chain=Virus comment="Drop Dumaru.Y" disabled=no dst-port=2283 protocol=tcp
add action=drop chain=Virus comment="Drop Beagle" disabled=no dst-port=2535 protocol=tcp
add action=drop chain=Virus comment="Drop Beagle.C-K" disabled=no dst-port=2745 protocol=tcp
add action=drop chain=Virus comment="Drop MyDoom" disabled=no dst-port=3127-3128 protocol=tcp
add action=drop chain=Virus comment="Drop Backdoor OptixPro" disabled=no dst-port=3410 protocol=tcp
add action=drop chain=Virus comment=Worm disabled=no dst-port=4444 protocol=tcp
add action=drop chain=Virus comment=Worm disabled=no dst-port=4444 protocol=udp
add action=drop chain=Virus comment="Drop Sasser" disabled=no dst-port=5554 protocol=tcp
add action=drop chain=Virus comment="Drop Beagle.B" disabled=no dst-port=8866 protocol=tcp
add action=drop chain=Virus comment="Drop Dabber.A-B" disabled=no dst-port=9898 protocol=tcp
add action=drop chain=Virus comment="Drop Dumaru.Y" disabled=no dst-port=10000 protocol=tcp
add action=drop chain=Virus comment="Drop MyDoom.B" disabled=no dst-port=10080 protocol=tcp
add action=drop chain=Virus comment="Drop NetBus" disabled=no dst-port=12345 protocol=tcp
add action=drop chain=Virus comment="Drop Kuang2" disabled=no dst-port=17300 protocol=tcp
add action=drop chain=Virus comment="Drop SubSeven" disabled=no dst-port=27374 protocol=tcp
add action=drop chain=Virus comment="Drop PhatBot, Agobot, Gaobot" disabled=no dst-port=65506 protocol=tcp
add action=return chain=Virus comment="Return From Virus Chain" disabled=no
/
# QOS Client 1-30 Fix 10/03/2015(D/M/Y) Sesuaikan dengan Bandwitch anda
/queue simple
add name="Client1" target=192.168.10.11 max-limit=512K/8M priority=7/8 comment="Client 1 - 10"
add name="Client2" target=192.168.10.12 max-limit=512K/8M priority=7/8
add name="Client3" target=192.168.10.13 max-limit=512K/8M priority=7/8
add name="Client4" target=192.168.10.14 max-limit=512K/8M priority=7/8
add name="Client5" target=192.168.10.15 max-limit=512K/8M priority=7/8
add name="Client6" target=192.168.10.16 max-limit=512K/8M priority=7/8
add name="Client7" target=192.168.10.17 max-limit=512K/8M priority=7/8
add name="Client8" target=192.168.10.18 max-limit=512K/8M priority=7/8
add name="Client9" target=192.168.10.19 max-limit=512K/8M priority=7/8
add name="Client10" target=192.168.10.20 max-limit=512K/8M priority=7/8
add name="Client11" target=192.168.10.21 max-limit=512K/8M priority=7/8 comment="Client 21 - 30"
add name="Client12" target=192.168.10.22 max-limit=512K/8M priority=7/8
add name="Client13" target=192.168.10.23 max-limit=512K/8M priority=7/8
add name="Client14" target=192.168.10.24 max-limit=512K/8M priority=7/8
add name="Client15" target=192.168.10.25 max-limit=512K/8M priority=7/8
add name="Client16" target=192.168.10.26 max-limit=512K/8M priority=7/8
add name="Client17" target=192.168.10.27 max-limit=512K/8M priority=7/8
add name="Client18" target=192.168.10.28 max-limit=512K/8M priority=7/8
add name="Client19" target=192.168.10.29 max-limit=512K/8M priority=7/8
add name="Client20" target=192.168.10.30 max-limit=512K/8M priority=7/8
add name="Client21" target=192.168.10.31 max-limit=512K/8M priority=7/8 comment="Client 31 - 40"
add name="Client22" target=192.168.10.32 max-limit=512K/8M priority=7/8
add name="Client23" target=192.168.10.33 max-limit=512K/8M priority=7/8
add name="Client24" target=192.168.10.34 max-limit=512K/8M priority=7/8
add name="Client25" target=192.168.10.35 max-limit=512K/8M priority=7/8
add name="Client26" target=192.168.10.36 max-limit=512K/8M priority=7/8
add name="Client27" target=192.168.10.37 max-limit=512K/8M priority=7/8
add name="Client28" target=192.168.10.38 max-limit=512K/8M priority=7/8
add name="Client29" target=192.168.10.39 max-limit=512K/8M priority=7/8
add name="Client30" target=192.168.10.40 max-limit=512K/8M priority=7/8
/
# QOS HTTP&HTTPS Fix 10/03/2015(D/M/Y)
/queue type
add kind=pcq name=PCQ_HTTP pcq-rate=3M pcq-classifier=dst-address
add kind=pcq name=PCQ_HTTPS pcq-rate=6M pcq-classifier=dst-address
/
/queue tree
add max-limit=10M name=All_Web parent=global priority=8
add name=QOS_HTTP packet-mark=QOS_HTTP parent=All_Web queue=PCQ_HTTP priority=8
add name=QOS_HTTPS packet-mark=QOS_HTTPS parent=All_Web queue=PCQ_HTTPS priority=8
/
# QOS Youtube/Video/Stream Fix 10/03/2015(D/M/Y)
/ip firewall layer7-protocol
add name=L7_Streaming regexp="videoplayback|video"
/
/ip firewall mangle
add action=mark-packet chain=postrouting layer7-protocol=L7_Streaming new-packet-mark=QOS_Streaming passthrough=no protocol=tcp disabled=no comment="QOS Client Youtube/Video/Stream"
/
/queue type
add kind=pcq name=PCQ_Streaming pcq-rate=6M pcq-classifier=dst-address
/
/queue tree
add max-limit=20M name=All_Streaming parent=global priority=7
add name=QOS_Streaming packet-mark=QOS_Streaming parent=All_Streaming queue=PCQ_Streaming priority=8
/
# QOS Download File Fix 10/03/2015(D/M/Y)
/ip firewall layer7-protocol
add comment="" name=L7_File regexp="\\.(exe|rar|iso|zip|7zip|flv|mkv|avi|mp4|3gp|rmvb|mp3|dat|mov)"
/
/ip firewall mangle
add action=mark-packet chain=postrouting layer7-protocol=L7_File new-packet-mark=QOS_File passthrough=no protocol=tcp disabled=no comment="QOS Client Download File"
/
/queue type
add kind=pcq name=PCQ_File pcq-rate=3M pcq-classifier=dst-address
/
/queue tree
add max-limit=20M name=All_File parent=global priority=6
add name=QOS_File packet-mark=QOS_File parent=All_File queue=PCQ_File priority=8
/
# Check Internet Fix 16/03/2015(D/M/Y)
# Check DNS 10s
# Check GateWay 1m
/system script
add name=WAN1_DNS policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive source=":local \
i 0; {:do {:set i (\$i + 1)} while ((\$i < 5) && ([/ping 203.144.207.49 in\
terval=2 count=5 interface=WAN1]<=1))};\r\
\n:if (\$i>=5) do={\r\
\n:log info \"WAN1 DNS Down\";\r\
\n/ip route disable [find comment=WAN1];\r\
\n} else { :log info \"WAN1 DNS UP\";\r\
\n/ip route enable [find comment=WAN1];\r\
\n}"
add name=WAN1_GW policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive source=":local \
i 0; {:do {:set i (\$i + 1)} while ((\$i < 5) && ([/ping 192.168.1.1 inter\
val=2 count=5 interface=WAN1]<=1))};\r\
\n:if (\$i>=5) do={\r\
\n:log info \"WAN1 GateWay Down\";\r\
\n/ip route disable [find comment=WAN1];\r\
\n} else { :log info \"WAN1 GateWay UP\";\r\
\n/ip route enable [find comment=WAN1];\r\
\n}"
add name=WAN2_DNS policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive source=":local \
a 0; {:do {:set a (\$a + 1)} while ((\$a < 5) && ([/ping 203.144.207.29 in\
terval=2 count=5 interface=WAN2]<=1))};\r\
\n:if (\$a>=5) do={\r\
\n:log info \"WAN2 DNS Down\";\r\
\n/ip route disable [find comment=WAN2];\r\
\n} else { :log info \"WAN2 DNS UP\";\r\
\n/ip route enable [find comment=WAN2];\r\
\n}"
add name=WAN2_GW policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive source=":local \
a 0; {:do {:set a (\$a + 1)} while ((\$a < 5) && ([/ping 192.168.2.1 inter\
val=2 count=5 interface=WAN2]<=1))};\r\
\n:if (\$a>=5) do={\r\
\n:log info \"WAN2 GateWay Down\";\r\
\n/ip route disable [find comment=WAN2];\r\
\n} else { :log info \"WAN2 GateWay UP\";\r\
\n/ip route enable [find comment=WAN2];\r\
\n}"
/
/system scheduler
add interval=10s name="CheckWAN1_DNS" on-event=WAN1_DNS policy=ftp,reboot,read,write,policy,test,password,sniff,sensitive
add interval=1m name="CheckWAN1_GW" on-event=WAN1_GW policy=ftp,reboot,read,write,policy,test,password,sniff,sensitive
add interval=10s name="CheckWAN2_DNS" on-event=WAN2_DNS policy=ftp,reboot,read,write,policy,test,password,sniff,sensitive
add interval=1m name="CheckWAN2_GW" on-event=WAN2_GW policy=ftp,reboot,read,write,policy,test,password,sniff,sensitive
/